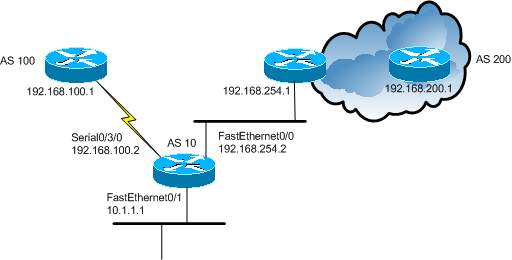
Router - BGP Conditional Advertisement
This configuration snippet shows how to setup an Internet facing router connected to two ISPs. One ISP is
connected with a 3Mb/s Ethernet connection, while the other provider is connected with a 1.544Mb/s T1.
Typically with BGP you can control which provider you send your output to, but you don't have much control
as to which provider you will receive your input from. In this scenario, the basic BGP configuration had
all of the input traffic coming in the lower speed T1. We tried to make suggestions to the ISP by prepending
the AS path multiple times, as well as various other methods of which none of them worked. The problem
is that since all of the traffic inbound was heading over the T1, the pipe was getting full and traffic was slowing
down. We couldn't take advantage of the 3Mb/s speed from the other provider. To solve this issue we used
BGP Conditional Advertisements. The idea is that we will only advertise our network to the ISP on the T1, if
we don't see the default route that is being advertised from the ISP on the 3Mb/s pipe. So since we do not
advertise our network to the T1 ISP, that ISP does not propagate routes for our network. So now all traffic
will flow inbound from the 3Mb/s pipe. If the connection to the 3Mb/s pipe is broken, or if we stop receiving
routing advertisements from the 3Mb/s provider, then the router will start automatically advertising our network
address to the T1 ISP, who will then propagate our routes. Then all the inbound traffic will once again flow back
in on the T1. This process takes about 60 seconds to converge. This is a good solution for unequal bandwidth
connections to providers where the inbound traffic is heavily weighted on the lower bandwidth connection.
# This configuration was taken from an ISR 2801 running 12.3(14)T4 SP Services.
# I always like debug and log informatio to show the actual date and time and it is also
# good security practice to make sure password-encryption is turned on.
service timestamps debug datetime
service timestamps log datetime
service password-encryption
hostname Internet-Rtr
logging buffered 4096 debugging
enable secret 5 $1$a5qj$ZSB5BF6RNzM26vsJTeiec0
aaa new-model
aaa authentication login default local
aaa authorization exec default local
aaa session-id common
resource policy
# To ensure accurate time reporting set the timezone properly as well set the new daylight savings time settings.
clock timezone est -5
clock summer-time EDT recurring 2 Sun Mar 2:00 1 Sun Nov 2:00
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
ip subnet-zero
# This is an Internet connected router to make sure source routing is turned off
no ip source-route
ip cef
no ip dhcp use vrf connected
ip domain name ciscoconfigs.net
no ftp-server write-enable
# Defined local usernames with two different levels of access.
username admin privilege 15 password ciscoconfigs
username monitor privilege 9 password ciscoconfigs
archive
log config
logging enable
# This interface is connected to the provider in Autonomous System 200. This provider is bringing in a 3Mb/s
# connection over Cat5. We filter the inbound traffic using access-list 110.
interface FastEthernet0/0
description Connection to 3Mb/s provider
ip address 192.168.254.2 255.255.255.252
ip access-group 110 in
speed 10
full-duplex
# This interface is the inside network. Normally this would be a public IP address. We simply changed it
# to protect the innocent ;)
interface FastEthernet0/1
description Inside Interface
ip address 10.1.1.1 255.255.255.0
speed 100
full-duplex
# This interface is connected to the provider in Autonomous System 100. This provider is bringing in a 1.544Mb/s
# connection over a T1. Again we filter inbound traffic using access-list 110
interface Serial0/3/0
description Connection to 1.544Mb/s provider
ip address 192.168.100.2 255.255.255.252
ip access-group 110 in
service-module t1 timeslots 1-24
# Here is the BGP section. It is broken into certain sections. The first few lines deal with general BGP parameters.
# Then there are specific sections for each provider. Router BGP 10 tells the router that we will run the BGP
# protocol and that our Autonomous System number is 10. BGP normally only advertises a route if it is already
# known via an interiorl routing protocol (OSPF, EIGRP, RIP, etc.) The no sync command means that this
# BGP process can advertise a route even if it is not in an interior routing protocol. The log-neighbor-changes will
# kick off a log entry when the neighbor connections go up and down.
router bgp 10
no synchronization
bgp log-neighbor-changes
# In BGP the network command works differently than in other routing protocols. Normally the network command
# defines which interfaces will participate in the given routing protocol. For BGP the command identifies the
# network that will originate from this router. This is basically the network we want to advertise to the two
# providers. So in this case we want to advertise our network to the providers.
network 10.1.1.0
# Now the following statements are specific to the neighbor in AS 100 across the T1 pipe. The first statement
# simply defines the neighbor as well as that neighbors AS number. The second statement assigns a
# Cisco defined BGP metric called Weight to routes that are being advertised from this neighbor. In this
# case we have asked the provider to only provide us with a default route since we are not a transit AS.
# So when that provider advertises a default route to us, we will assign the weight of 500 to it. Good practice
# for BGP peering is set up a distribution list that defines what networks you will advertise to the provider.
# In this case distribute-list command says that we will only advertise routes that are in access-list 15, which
# simply has our public address. (In this case it is 10.1.1.0 though). The final command - advertise-map is
# only listed on this peer.
#
# First the problem - After we set up basic BGP with each provider we found that all traffic was coming back
# in through this provider. The problem is that this is the 1.5Mb/s provider not the 3Mb/s provider. So basically
# we are choking our inbound traffic. Given this traffic pattern we decided that it would be best to force the
# inbound traffic to come in through the other provider. This statement helps us acheive our goal. This is
# what is says. This router will only advertise "networks defined in the route-map named ADVERTISE" if
# and only if "routes that are defined in the route-map named NON-EXISTS" do not appear in the BGP
# routing table. For instance if the other provider (AS 200) is providing us with a default route, then that connection
# is up and running fine, therefore we will not advertise our network to this provider (AS 100). If we don't advertise
# our network to this provider (AS 100) then he will not advertise it out, so no one knows about this route into our
# network thereby forcing inbound traffic to come in from the other provider (AS 200) who has the bigger pipe.
#
# Now if the BGP peer connection goes down to the neighbor in AS200, we will no longer receive a default route
# from that neighbor. In that case the default route which is defined in the NON-EXIST route map will not be
# the BGP routing table. In that case we will start advertising our network to the provider in AS 100 since our
# network is listed in the route map ADVERTISE. There is around 30-60 secs of down time as things converge.
neighbor 192.168.100.1 remote-as 100
neighbor 192.168.100.1 weight 500
neighbor 192.168.100.1 distribute-list 15 out
neighbor 192.168.100.1 advertise-map ADVERTISE non-exist-map NON-EXIST
# Here are are peering statements to the neighbor in AS 200 across the 3Mb/s pipe. Again we define that
# the neighbor and define his AS number as 200. Normally eBGP neighbors are directly connected. In this
# case the BGP peer in AS 200 is not directly connected to us. We need to define this with the use of the
# ebgp-multihop command. We then added a weight of 1000 to any routes advertised to us from this neighbor.
# If we have identical routes advertised to us from both providers, the route from this neighbor will take
# precedence since it will have a higher weight. Since we are only getting a default route from each
# provider will choose to send our outbound traffic out over this peer as long as they are connected.
neighbor 192.168.200.1 remote-as 200
neighbor 192.168.200.1 ebgp-multihop 255
neighbor 192.168.200.1 weight 1000
neighbor 192.168.200.1 distribute-list 15 out
no auto-summary
ip classless
# Since we are not direclty connected to the BGP neighbor in AS 200, we need to add a static route so
# we can reach them.
ip route 192.168.200.1 255.255.255.255 192.168.254.1
# This is an AS-PATH access-list that defines an AS-path that last came from AS 200.
ip as-path access-list 1 permit ^200
no ip http server
ip http authentication local
no ip http secure-server
ip http timeout-policy idle 600 life 86400 requests 10000
# Normally this router would be on the outside of a firewall. This access-list is used on the virtual
# terminal lines to only allow this address to be able to gain telnet access.
access-list 2 permit 10.1.1.2
# This acl is used in the BGP distribution-list defined in the router BGP section above.
access-list 15 permit 10.1.1.0
# Used in the route map ADVERTISE to list the network that we want to advertise via BGP if the
# conditions are met.
access-list 60 permit 10.1.1.0 0.0.0.255
# Used in the route map NON-EXIST to list the network that we want to make sure does not exist before
# we advertise the route in ADVERTISE.
access-list 65 permit 0.0.0.0
# Access-list 110 is not 100% accurate for this snippet. In this example we have changed the IP addresses
# to all belong to RFC 1918 private addresses. The idea behind this access-list is to block any inbound
# packets that are coming from a null address, a loopback address, any of the RFC 1918 addresses because
# these should not be routed on the Internet anyways (however most ISPs do not perform ingress filtering so
# they typically aren't stopping someone from sourcing packets with these addresses), and then finally we
# want to block anyone from sending packets in sourced with your public address. In this example it would
# be 10.1.1.0 network, however, normally this would be a public address and the 10 net should be blocked
# from coming in. So the X.X.X.0 should be your public address. So basically we filter out a lof garbage from
# coming in and then let everything else in. Hopefully there is a firewall behind this router as well.
access-list 110 deny ip host 0.0.0.0 any log
access-list 110 deny ip 127.0.0.0 0.255.255.255 any log
access-list 110 deny ip 10.0.0.0 0.255.255.255 any log
access-list 110 deny ip 172.16.0.0 0.15.255.255 any log
access-list 110 deny ip 192.168.0.0 0.0.255.255 any log
access-list 110 deny ip X.X.X.0 0.0.0.255 any log
access-list 110 permit ip any any
access-list compiled
# It is good security practice to set up your read and write community strings to something other than
# public and private. In this example we also used the access list that defines which hosts we
# will actually accept an snmp request from.
snmp-server community ciscoconfigs-readonly RO 2
snmp-server community ciscoconfigs-readwrite RW 2
snmp-server enable traps tty
# Here is the route-map that BGP Conditional Advertisement will use. This matches a default
# route coming from AS 200.
route-map NON-EXIST permit 10
match ip address 65
match as-path 1
# Here is the other route-map that BGP Conditional Advertisement will use. This matches our
# network that we want to advertise.
route-map ADVERTISE permit 10
match ip address 60
control-plane
# Since we have created the username monitor above and gave it a privilege level of 9, we are
# defining the types of commands that a level 9 user can issue. A level 15 can do anything.
# This way we set administrative access to this box that can look but not change anything.
privilege exec level 9 traceroute
privilege exec level 9 ping
privilege exec level 9 show startup-config
privilege exec level 9 show running-config
privilege exec level 1 show
# On the console and virtual terminal ports 0 - 4 we set the login to local so that we will use user authentication
# against the local database. A username was added near the beginning of this configuration. In addition
# the logging synchronous command helps you type in commands when the screen is scrolling. If you are halfway
# through your command and a console message popped up on the screen it would then take the part of the
# command that you already typed in a put it on a new line for you instead of breaking your command accross
# console messages.
line con 0
login local
logging synchronous
line aux 0
line vty 0 4
access-class 2 in
login local
logging synchronous
transport input telnet
# It is always good to have a time server configured so all of your network devices will have the correct
# time. This is important when trying to correlate events between devices and logs.
ntp server 128.105.39.11
end
 RSS Feed
RSS Feed